Descriptif de l’Enseignement de la Filière Génie Cybersécurité (GCYS) / Engineering program in Cybersecurity
Coordinatrice : Pr. LAZAAR Saiida
1. Objectifs de la formation
In today’s world, there is an ongoing surge of growth and progress, driven by rapid technological advancements and innovations. The need for digital data exchange has increased over the past decade, driven by the digital transition. It is therefore essential to secure digital data, networks, applications, and systems against cyber attacks. This degree is part of this perspective, the main objective is to acquire a strong knowledge of the concepts and techniques of cybersecurity.
The training will cover a very broad and specific spectrum of courses in the field of cybersecurity, and will revolve around IT, networks, and security based on cryptography and AI. In parallel, the training will cover methods and standards of cyber risk policy and management, threat intelligence, and security of Industry 4.0. This training enables individuals to develop a comprehensive understanding of the technical and technological environments in which companies operate and acquire advanced technical and methodological skills for cybersecurity. The cybersecurity experts will possess advanced technical skills in information systems to collect, identify, analyze, and interpret various cyber threats that may affect computers, mobile phones, connected objects, or industrial systems. They then define and implement an information systems security strategy to prevent or respond to encountered threats effectively. The graduates will have the essential assets to take charge of cybersecurity projects, and to participate in the development of solutions and approaches responding to the challenges launched in the cyber defense field, both nationally and internationally.
2. Compétences à acquérir
This training will allow engineering students to acquire solid and cutting-edge skills in the field of cybersecurity. More specifically, skills will be acquired in information system security, applied cryptology, machine learning, intelligent systems, IoT security, web security, mobile application security, network and system security, data centers, system administration, and programming.
These skills will enable learners, and future business executives, to provide solutions in the field of security in the digital world, conduct cyber risk management studies, and propose reliable security policies. The skills acquired will meet the needs and expectations of different sectors of the country (academic, ministerial, technological, industrial, banking, etc.)
Main technical skills to acquire:
- Master the fundamental technical concepts of cybersecurity: safety mechanisms, cryptography, artificial intelligence tools for malware analysis …, intrusion detectors, norms, and standards ;
- Understand the ethical issues in computer security and pentesting ;
- Assess the IT security risks of an organization;
- Master malware analysis, malicious attack simulation tools, and threat intelligence ;
- Be able to perform IT security audits and conduct intrusion tests ;
- Master the technical and legal concepts of protecting an organization’s data and technological assets.
3. Débouchés de la formation
- Cybersecurity expert, Systems and Network Engineer, Cryptologist Engineer, Artificial intelligence Engineer, Security Administrator, Cybersecurity Consultant, Project Manager, Cybersecurity Project Director, IS Manager, Security Designer / Architect, IS Security Manager, Cybersecurity Auditor, etc.
- Expert Cybersécurité, Ingénieur Systèmes et Réseaux, Ingénieur Cryptologue, Ingénieur Intelligence Artificielle, Administrateur Sécurité, Consultant Cybersécurité, Chef de Projets, Directeur de Projets Cybersécurité, Responsable SI, Concepteur / Architecte Sécurité, Responsable Sécurité SI, Auditeur Cybersécurité, etc.
4. Semestres
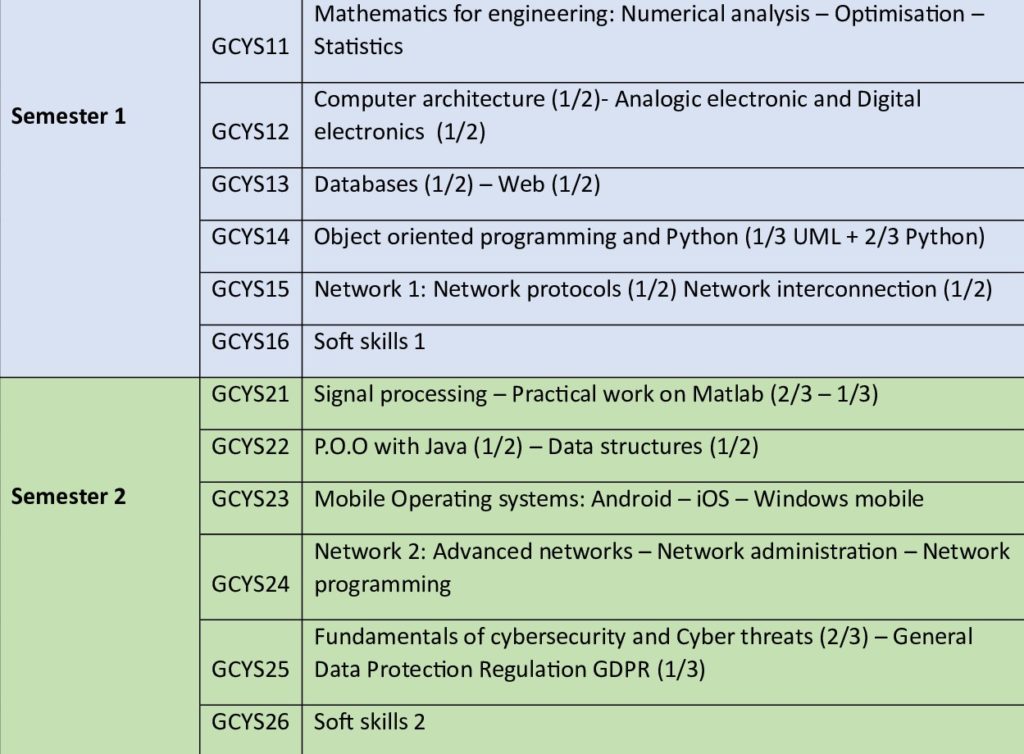
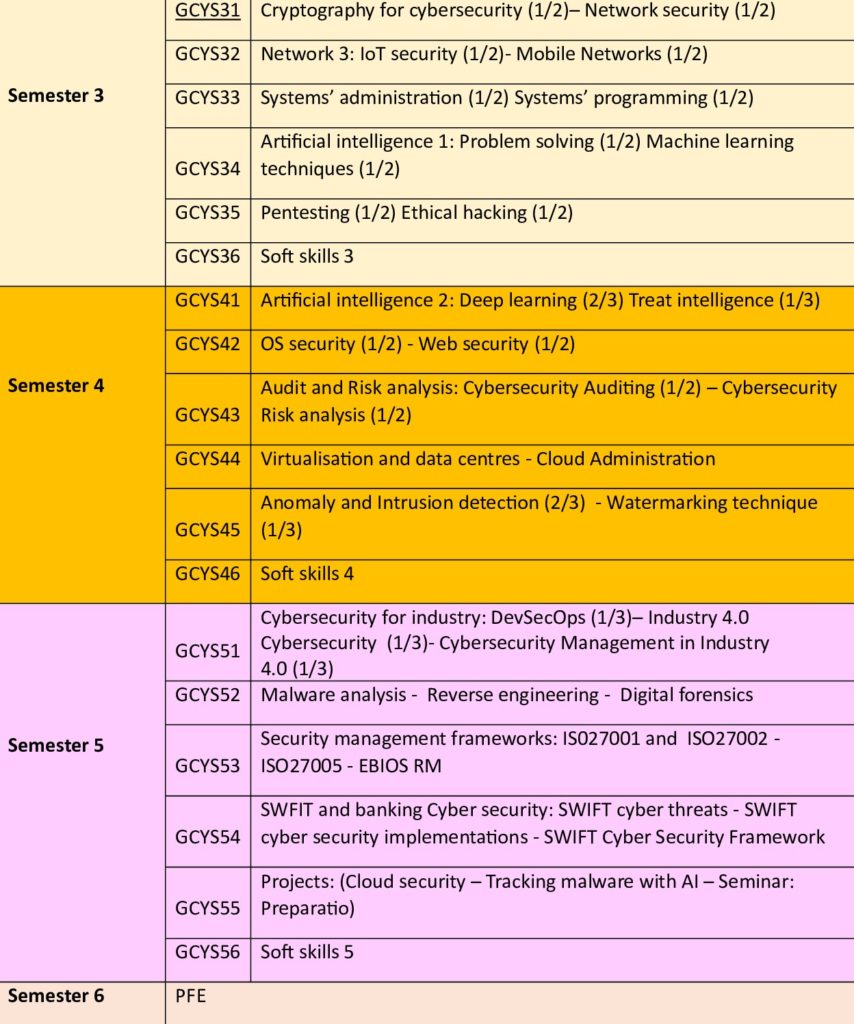
5. Sommaire des modules
| Descriptif du Module n° : | Intitulé du Module |
|---|---|
| M111 | Mathematics for Engineering: Numerical analysis Optimisation Statistics |
| M112 | Computer Architecture Analog Electronics And Digital Electronics |
| M113 | Databases and WEB |
| M114 | Object oriented programming UML Python Language |
| M115 | Network 1: Network Protocols & Network Interconnection |
| M116 | Management of Companies |
| M128 | Signal processing |
| M127 | P.O.O with Java and Data Structures |
| M128 | Mobile Operating systems |
| M128 | Networks 2: Advanced networks Network Administration Network programming |
| M127 | Fundamentals of cybersecurity and Cyber threats – General Data Protection Regulation |
| M127 | COMPANY MANAGEMENT I |
| M231 | Cryptography for cybersecurity and Network security |
| M236 | Network 3: IoT Security & Mobile Networks |
| M233 | ADMINISTRATION AND SYSTEM PROGRAMMING |
| M235 | Artificial Intelligence 1 |
| M232 | Pentesting and Ethical hacking |
| M234 | MANAGEMENT II |
| M242 | Artificial Intelligence 2 |
| M241 | OS security Web security |
| M244 | Audit Risk analysis |
| M246 | Virtualisation and data center Cloud administration |
| M245 | Anomaly and intrusion detection – Watermarking |
| M243 | LANGUAGE AND COMMUNICATION II |
| M353 | Cybersecurity for industry |
| M355 | Malware analysis Reverse engineering Digital forensics |
| M351 | Security management framworks |
| M354 | SWIFT and banking cybersecurity |
| M352 | Projects and preparation to certification |
| M356 | Management 3 |
